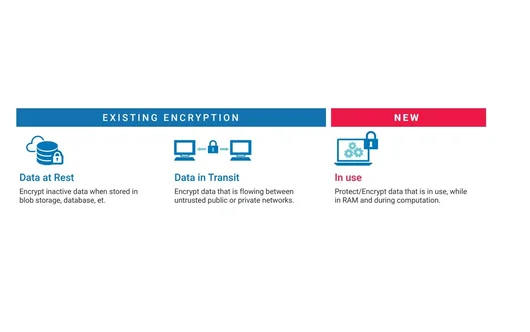
Definition
A new term like Confidential Computing often comes with different definitions that depend on the perspective on the subject.
- Google [1] defines it as described above: breakthrough technology that allows you to encrypt data in use, during processing .
- Microsoft [2] goes a step further and introduces another aspect in addition to securing data in use: secure privacy and analysis of data by multiple parties.
- Confidential Computing Consortium [3]: enables new public cloud scenarios, such as placing extremely sensitive data in the cloud, and scenarios where multiple parties, without having to expose data, can still link things together (multi-party computing of MPC).
These definitions include two topics:
- The principle of securing data in use
- The possibilities of secure multi-party computation
TNO defines MPC as follows [4]: MPC is a "toolbox" of cryptographic techniques that allows multiple parties to jointly compute data, as if they had a shared database. Because the data is protected in a cryptographic way, it can be analyzed without the parties ever being able to see other people's data. The participating parties determine who is allowed to see the results of the computation.
Below I discuss data in use.
When necessary?
An important application of Confidential Computing for data in use is the scenario where public cloud services can be used for sensitive data, such as medical data, despite their public nature. Measures to guarantee privacy for data at rest and for data in transit can already be taken effectively. Through special infrastructure, so-called hardware security modules, it is possible to create even greater security. The weak spots that remain are the processor and the memory, because in order to execute the software, the data has to be decrypted. And although it is far from easy to read the memory of another process, it cannot be 100% excluded. For example, if new vulnerabilities are discovered and not yet closed.
Trusted Execution Environments
Modern CPUs now have a technique built in that allows the processor to encrypt part of the memory while processing data. The encryption can only be done by the processor itself and decryption is only possible if the public key of the same processor is used. In addition, features have been added so that you can be sure that only software approved by customer and vendor is executed. During processing, the data is shielded and only the outcomes are brought out. This technique is also called processing in Trusted Execution Environments (TEEs or enclaves).
According to Edgeless Systems , a German company that develops open source applications based on this technology, there are four important preconditions for meeting strict privacy requirements:
- Isolation: running a program and processing data in a special process by the CPU, the trusted enclaves.
- Runtime memory encryption: encrypted memory content.
- Sealing: ability to secure status outside the trusted enclave with encryption .
- Remote attestation: guarantee that processing is carried out in a trusted enclave with a known and published program.
Conclusion
The core of this story is that with Confidential Computing, it is possible to process data in an otherwise untrusted environment, such as a public cloud or a competitor's computer, without violating privacy or compromising security. This allows a public cloud to meet the same privacy requirements as a private data center.
Next time more on multi-party computation.